Configure an extranet web application for Claims based authentication using AD and Forms. Store membership credentials in a SQL database. Manage members through IIS Manager.
There are not a lot of differences with configuring FBA for SharePoint 2010 compared to 2007, but there are a few. For instance, SharePoint 2010 no longer supports “classic FBA”, rather forms based authentication is provided through Claims Authentication. There is also the introduction of the Secure Store Service which is the next-gen of the Single Sign On service of old.
Step 1. Configure SQL Database for FBA
The creating the database is exactly the same as what we did for MOSS 2007. The database is still created using the ASP.NET SQL Server Setup Wizard. This is launched from the .NET 2.0 Framework folders on the server at:
“C:\Windows\Microsoft.NET\Framework\v2.0.50727\aspnet_regsql.exe”
After clicking aspnet_regsql.exe this will take you through the steps and will build out the SQL database for you.
Step 3. Create SQL user
Go back in object Explorer and expand “Security –> Logins”. Right-click logins and select “New Login…” On the New Login page, enter a username, password on the general page, clear all three password options for policy, expiration, and enforce change. Hit Ok and we have our SQL user.
Step 4.Add SQL user to membership database
Now, navigate to the database we created for our membership earlier (PRAVIN_FBA), and expand to Security-> Users. Right-click on Users and select New User….
Enter the name, select Login name, and give this fella the role “db_owner”.
Step 5. Configure Central Admin Web Site to use SQL Membership Provider
SharePoint web sites out of the box are configured to use Active Directory. So you may be wondering why we’re configuring Central Admin to use FBA when we don’t really want to login in as an FBA user. Well, we actually don’t want to configure it to login as a forms user, but we do need to be able to add users from our membership database when configuring site collection admins, and the like.
So all we want to do is tell the Central Admin web application to use our SQL membership provider as well as AD, so when you use the people picker to select users, it will provide results from our membership database.
Open IIS Manager on the WFE server (if more than one, then this needs to be done on every FWE that has Central Admin. The same goes for the proceeding steps for the other web applications).
Select the SharePoint Central Administration v4 site. On the Home Page, you’ll see many options for ASP.NET and IIS. The ones we’re concerned with are
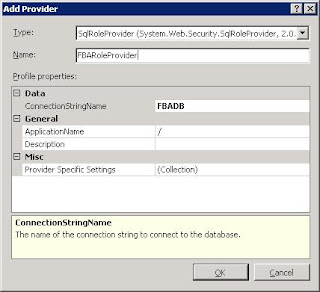
Step 7.Add Role Provider
Go back to the Web Application page and open up Providers page. Here we will create a provider for Roles and Users. Set feature to .NET Roles and click Add… in the Actions pane to add a new role provider. I called it FBARoleProvider and selected the right type and connection string.
Ensure you provide an ApplicationName so the provider knows what uses to authenticate. For a good explanation on why you need this,
Step 8.Add Membership Provider
Now set feature to .NET Users and click Add… from the actions pane to add a membership provider.
Step 9. Select the correct type and connection string, and whatever behaviors you choose.
That’s it for the providers for Central Admin.To verify that all looks ok, we can check the web.config of the web application. To get to the right web.config, right-click on the web application under sites, and select Explore.
In the web.config, you’ll see sections for the connection string and the providers. The
Central Admin Web.config
<roleManager>
<providers>
<add name="FBARoleProvider" type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" applicationName="/" connectionStringName="FBADB" />
</providers>
</roleManager>
<membership>
<providers>
<add name="FBAMembershipProvider" type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" applicationName="/" connectionStringName="FBADB" enablePasswordReset="true" enablePasswordRetrieval="false" passwordFormat="Clear" requiresQuestionAndAnswer="false" requiresUniqueEmail="false" />
</providers>
</membership>
You should also see a
Step 10. Configure Secure Store Web Service to use SQL Membership Provider
Everything we did for Central Admin site, we are going to do for the SecurityTokenServiceAppliaation which is in the SharePoint Web Services application.
Do same which are we did for Central Administrator repeat the step 6, 7, 8:
Create the connection string follow step 6
Add the .NET role provider follow step 7
Add the .NET users provider follow step 8
Web Service => Security Token ServiceApplication web.config look like
<membership>
<providers>
<add name="FBAMembershipProvider" type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" applicationName="/" connectionStringName="FBADB" enablePasswordReset="true" enablePasswordRetrieval="false" passwordFormat="Clear" requiresQuestionAndAnswer="false" requiresUniqueEmail="false" />
</providers>
>
<providers>
<add name="FBARolePRovider" type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" applicationName="/" connectionStringName="FBADB" />
</providers>
>
Step 11. Create Extranet Web Application
Ok, finally we are ready to create our web application (called SharePoint – FBA) that will use FBA authentication.
In Central Admin, Select the “Application Management => Manage web applications”. Select New from the ribbon to create a new web application.
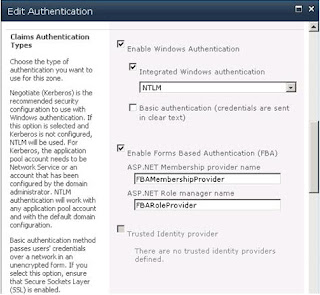
Select “Claims Based Mode Authentication” as Authentication Type. Select values for all the other options until you get to the “Enable Forms Based Authentication”.
Add the values we created earlier in the section “Enable Forms Based Authentication” for role and membership provider.
Step 12.Create Site Collection
Once the application is created, we should create a site collection. Go to the Create Site Collection page from the Manage Applications section in Central Admin. Select the team (or blank, or whichever you choose) template then select the site collection administrator. At this point, we should be able to select from our SQL membership users. Enter a user you know exists in the membership database and see if you can resolve the names.
I have a user with the same name in both AD and SQL, so I know I am hitting both.
At this point we have told SharePoint what role providers to use for the web app, but we still need to configure the web app through IIS manager to bind the providers.
Step 13.Configure Membership Providers for Web App through IIS
In IIS Manager, browse to the new site SharePoint – FBA. For our new FBA site we need to do the following:
Ø Add connection string
Ø Add Providers for members and roles
Ø Configure .NET Roles
Ø Configure .NET Users
Ø Set Authentication to Forms and Integrated
Add User as Site Collection Admin
Add Connection String
Same as we have done before.
Step 14. Add role and user providers
Again, same as what we did before. Open Providers page and add an entry for our role and user providers.
Step 15. Configure .NET Roles
This and the next steps are not required for the other two web applications we configured (Central Admin and SSS). Open the .NET Roles page for our web application. You will receive a warning that the default role provider is not trusted. WE just need to set our default role provider to FBARoleProvider.
We do not have any roles in our database at this point, so let’s create two (StandardUser, SuperUser) by clicking Add… in the actions pane.
Note:Add the role provider and membership provider in “<peoplepickerwildCard>” in both your site web.config and Central Admin web.config
<peoplepickerwildCard>
<add key="FBADBMembershipProvide" Value= "%" />
<add key="FBADBRoleProvide" Value= "%" />
</peoplepickerwildCard>
Step 16. Configure .NET Users
Now we need to do the same for .NET Users. Open the .NET Users page. You will get a similar warning saying the default is not trusted. Set the default provider to FBAMembershipProvider. If you had members in the database, you would now see them listed. Assuming you doesn’t let’s add some. Click Add… from the Actions pane to add users, and assign them roles.
Step 17. Set Authentication
SharePoint should have done this when you created the web application, but let’s confirm. From the web application home page in IIS Manager, select Authentication under the IIS section. Confirm that the web application has both Integrated and Forms enabled.
Step 18. Add User as Site Collection Admin
Now that we have everything hopefully configured correctly, we can go back to SharePoint Central Admin and add our new user as the Site Collection Administrator. From Central Admin Application Management page, click Change site collection administrators. Select SharePoint – FBA root site collection, and add our new user.
Now let’s test all this business by trying to login. Browse to your site and select to login as a forms user.
I am authenticated ok, but am not allowed in, even though I’m a site collection admin?!
Here’s the caveat – In order for you to use IIS Manager to manage your SQL users, you need to set the default provider to our Forms provider, i.e. FBAMembershipProvider. In order for it to work we need to set it to the SharePoint claims provider. Go back to .NET Users and reset the default provider to “i” which is for the Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider
To verify all of the above: here are the three web.config files in play:
Web Application (SharePoint – FBA) web.config
<membership defaultProvider="i">
<providers>
<add name="i" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider, Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" />
<add name="FBAMembershipProvider" type="System.Web.Security.SqlMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" applicationName="/" connectionStringName="FBADB" enablePasswordReset="true" enablePasswordRetrieval="false" passwordFormat="Clear" requiresQuestionAndAnswer="false" requiresUniqueEmail="false" />
<providers>
membership>
</roleManager cacheRolesInCookie="false" defaultProvider="FBARoleProvider" enabled="true">
<providers>
<add name="c" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthRoleProvider, Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral, PublicKeyToken=71e9bce111e9429c" />
<add name="FBARoleProvider" type="System.Web.Security.SqlRoleProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" applicationName="/" connectionStringName="FBADB" />
</providers>
</roleManager>
Now let’s try to login again.
I hope this help……..
Special Thanks to Mr. Dheeraj Palande And Mr.Abhay Wad.